What Is Baiting in Cyber Security?
9 July 2025
Cyber criminals are constantly evolving, using an increasingly wide range of tactics to achieve malicious goals. Baiting is a type of social engineering technique, alongside phishing, and typically exploits an individual’s greed or curiosity to get them to compromise their cyber security. Just over 35% of 10,500 organisations surveyed in 2021 were targeted by a bait attack in one month, showing just how prevalent these kinds of cyber attacks have become.
So, what is baiting in cyber security, and how does a bait attack work?
Baiting attacks lure users by offering enticing rewards or seemingly valuable items. This ‘bait’ can range from anything between a false ad offering a free music download to an abandoned USB drive in an employee car park. Once the user has plugged in the physical device or clicked on a link, hackers can then install malware or ask for personal information, which they will later misuse.
Read on to find out more about what baiting is, the different types, illustrative examples and how you can protect yourself against baiting attacks.
Jump to a section:
- What is Baiting?
- Who Does Baiting Target?
- How Does Baiting Work?
- What Are the Different Types of Baiting?
- Examples of Baiting Attacks
- How to Prevent Baiting Attacks
- Protect Yourself From Baiting and Other Cyber Security Threats
- Baiting FAQs
What is Baiting?
Baiting is a social engineering tactic where attackers trick users by offering something enticing in exchange for access or information. For example, an ad or comment left in a social forum, such as Reddit, might promote a free software download, such as a free version of a popular video-editing software. However, rather than downloading the software, the file downloads a Remote Access Trojan (RAT), which cyber criminals can then use to spy on the user and steal passwords and other sensitive information.
Baiting attacks typically involve persuading users to divulge sensitive information (such as an email address or phone number), download malware or pay money. They typically rely on human nature and exploit curiosity or greed to achieve their nefarious goals. According to Verizon’s 2024 Data Breach Investigations Report, 68% of data breaches involved a human element. Both individuals and businesses can be targeted by baiting attacks.

How Baiting is Different from Other Social Engineering Techniques?
Social engineering techniques are deceptive tactics designed to manipulate people into compromising their personal data or cybersecurity. Baiting is different from other types of social engineering attacks because it relies on enticing individuals with an offer or reward to lure them into a compromising position. Here’s a breakdown of how baiting compares to other social engineering techniques:
| Technique | Tactic | User Motivation | Delivery Methods |
| Baiting | Offers something enticing (a free gift, leaked information or fake software) | Curiosity, greed | USB devices, fake download links and ads |
| Phishing | Cyber criminals pose as trusted sources to obtain sensitive data | Fear, urgency, trust | Emails, texts, phone calls, fake websites and messaging platforms |
| Whaling | Targets high-profile individuals with highly customised phishing | Authority, responsibility | Spear-phishing emails that impersonate an associate of the victim |
| Tailgating | Follows authorised personnel into secure areas without credentials | Politeness, trust, unawareness, carelessness | Physical intrusion, door access |
| Quid Pro Quo | Promises a benefit in exchange for information or access | Reciprocity, helpfulness | Phone calls, emails (e.g., fake tech support) |
| Vishing | Uses voice calls to impersonate trusted figures and extract data | Trust, fear, urgency | Phone calls (e.g., from criminals pretending to be from the victim’s bank) |
| Smishing | Sends fake SMS messages with malicious links or prompts | Urgency, curiosity | SMS, WhatsApp, or messaging platforms |
If you’d like to learn more about other types of social engineering attacks, have a look at our blog, ‘What Is the Difference Between Phishing and Blagging?’.
Who Does Baiting Target?
Baiting can target both individuals and businesses to steal confidential or sensitive information or install malicious software. Here’s a bit more information about the targets of baiting:
- Individuals: Targeted for personal data or identity theft.
- Businesses: Employees may be baited to access company data or finances.
- Organisations and government entities: Targeted for espionage, financial gain, or political motives.
How Does Baiting Work?
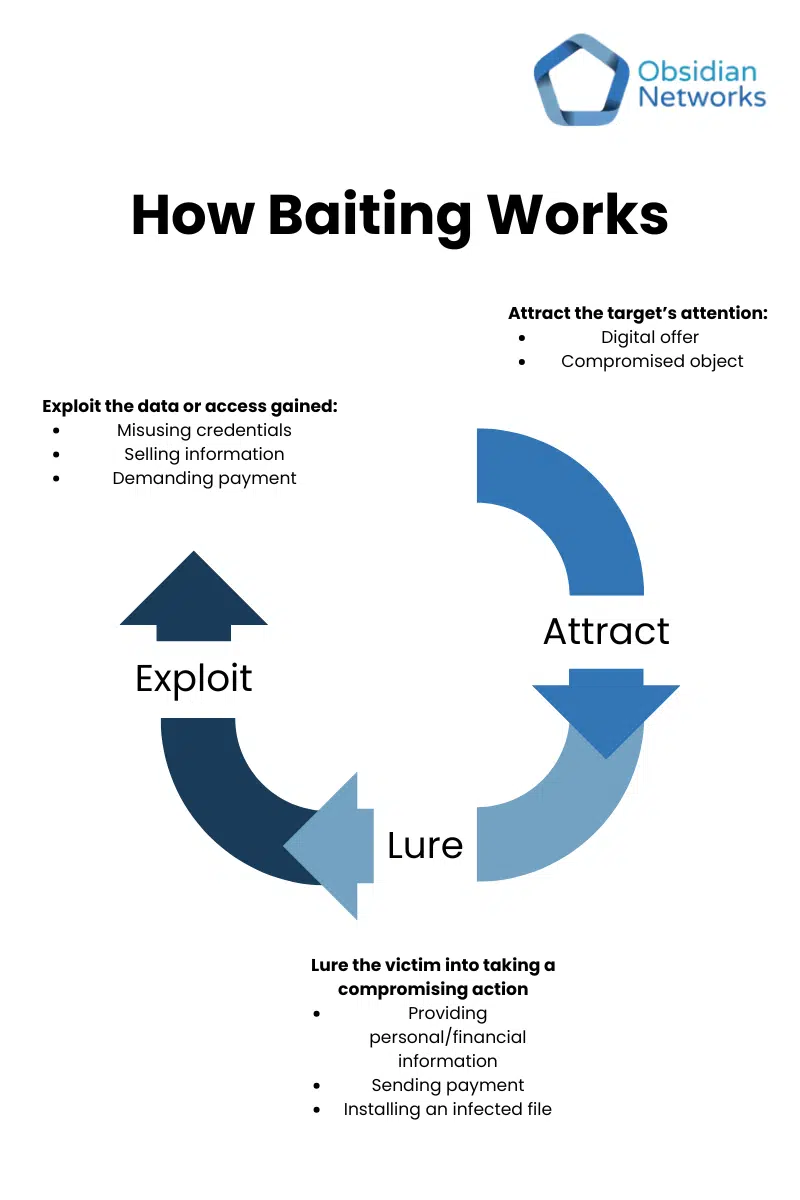
Baiting exploits a victim’s curiosity or greed. A baiting attack typically unfolds in three stages:
- Attract the target’s attention: This can be achieved through an attractive digital offer, such as an invitation to click on a link to enter a contest, or a compromised object, like a USB drive with malicious malware left in a public location.
- Lure the victim into compromising their cyber security: The next step is to entice the victim into taking a compromising action. This could be providing their financial or personal information, sending a payment or installing an infected file.
- Exploit the data or access gained: Once the victim’s cyber security has been compromised, the attacker will exploit this compromise according to the goal of the attack. This might include misusing stolen credentials, selling personal information, demanding payments or using the victim’s system for future attacks.
What Are the Different Types of Baiting?
Baiting attacks can take several different forms, some of the most common types include:
- Spear baiting
- Physical baiting
- Clickbait
We go over these in more detail below.
Spear Baiting
This form of baiting targets a specific organisation or business and its employees. Attackers conduct comprehensive research to make the lures more convincing and highly targeted. This might include fake job offers, access to industry-specific software or the impersonation of trusted individuals. Spear baiting attacks tend to be highly effective and are usually carried out in order to gain access to confidential or financial company data, login credentials or the company’s network.
Physical Baiting
While most baiting attacks occur online through tempting offers, they can also involve physical items. Most commonly, this is through a USB stick or QR code left in a public place. Cyber criminals exploit human curiosity, hoping someone will plug in their infected USB stick or scan their code, which leads to a malicious website or installs infected software. During a study conducted at the University of Illinois, 45% of 297 dropped USB drives were plugged in, while 20% of these ‘finders’ opened files, clicked links or sent messages to an email address on the drive.
Clickbait
This relies on sensational ads or headlines to trick users into clicking. Examples include:
- Phoney error messages or warnings
- Browser extension or add-on offers
- Free information or advice (e.g. on how to get rich quick)
- Free downloads of music, software or videos
- Lotteries or contest entries
- Products at extreme discounts
Examples of Baiting Attacks
Here are some illustrative examples of baiting attacks to help you better understand how they work:
- A malicious USB drive is left in the car park of an office building in the hope that an employee will assume it belongs to a colleague and plug in the device. Once plugged in, the drive can install spyware that gives the hacker access to the company’s internal systems.
- An online ad using clickbait tactics offers a free download of a recent blockbuster movie. Once clicked, it redirects the user to a malicious site that installs ransomware.
- An email offers a free iPhone in exchange for filling out a short survey. Contact information and card details are asked for to cover ‘shipping costs’.
- A Google Drive link is sent to an employee with an enticing title, such as ‘2025 Salary Review’ or ‘Redundancy Plan 2025’. When the employee clicks on the links, a keylogger is installed that records everything the employee types on their work computer.
- A pop-up disguised as a system alert urges the user to contact a ‘Microsoft-certified’ support number. Once clicked, the hacker can gain remote access to install spyware or demand payment for repairs or system upgrades.
How to Prevent Baiting Attacks
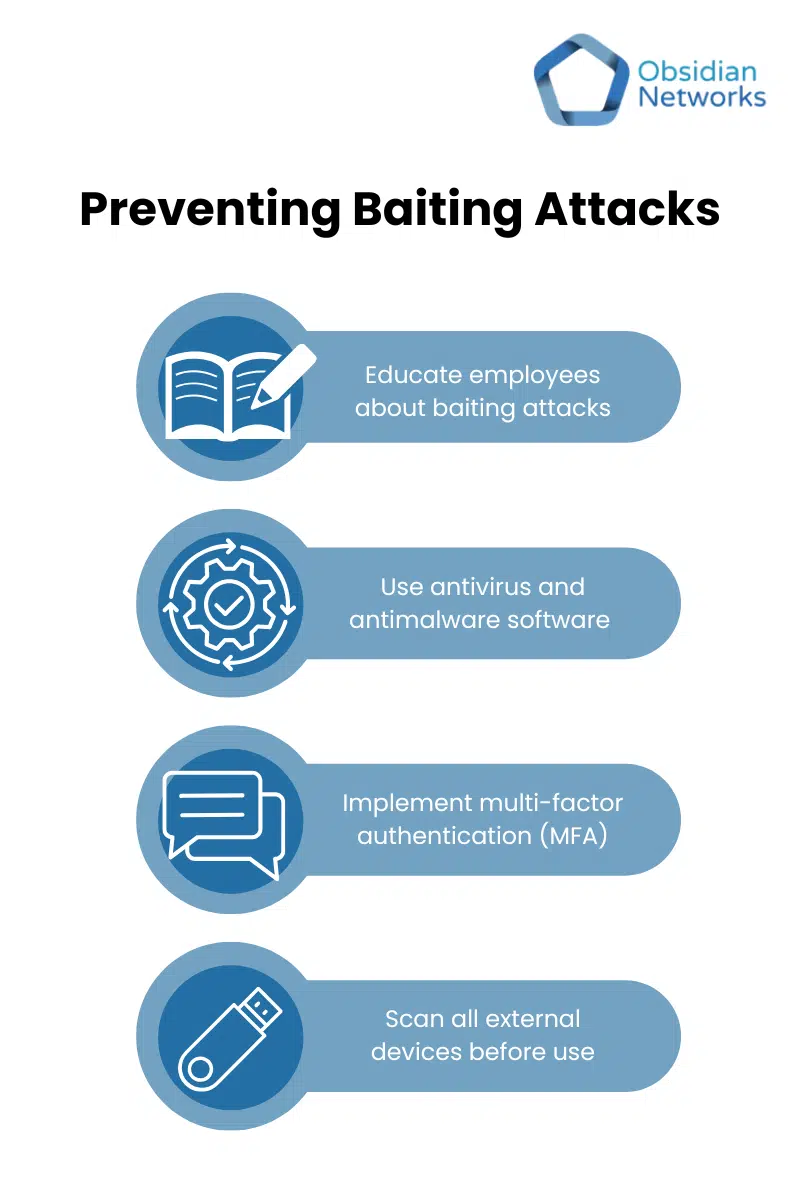
You can detect and prevent baiting attacks through a combination of training and security tools:
- Employee training: Teach staff to recognise baiting attempts, be sceptical of unknown devices and offers, and avoid interacting with suspicious messages and clicking on unknown links.
- Security tools: Use antivirus, antimalware software and firewalls. Scan all external devices before use and implement strict permissions and multi-factor authentication (MFA).
Protect Yourself From Baiting and Other Cyber Security Threats
At Obsidian Networks, we offer Cyber Essentials Certifications to help businesses protect themselves against baiting and other cyber attacks. The Cyber Essentials certification covers five technical controls that help protect organisations against 80% of the most common cyber attacks, and includes having malware protection in place to safeguard against baiting attacks.
We also offer comprehensive cyber security services, including cyber security monitoring, anti-virus and anti-malware software, and email scanning, to help protect your business from threats.
Whether you’re interested in a bespoke cyber security solution or would like to learn more about the Cyber Essentials Certification, get in touch with a member of our team today.

Baiting FAQs
What Makes Baiting Different From Phishing?
While baiting and phishing are both forms of social engineering attacks, they differ in their primary tactic:
- Baiting exploits human curiosity or greed by offering something of ‘value’ to entice users into compromising their cyber security.
- Phishing uses deception to trick users into revealing information or clicking on malicious links.
However, there are many overlaps between different social engineering techniques, and many hackers will use a combination of tactics to achieve their aims.
What Is ‘Digital Baiting’ vs ‘Physical Baiting’?
Digital baiting involves online traps (e.g. fake downloads), whereas physical baiting involves tangible items like USBs or QR codes.
Can Baiting Happen Over Social Media?
Yes. Fake offers or clickbait on platforms like Facebook or LinkedIn are common baiting tactics. Typically, these will offer an enticing but false reward to lure users into clicking on malicious links.
Is Baiting Used During Penetration Testing?
Yes, baiting can be simulated during penetration testing to ensure a company’s cyber security defences are adequate. Simulated baiting attacks can be an incredibly useful tool to test your business’s automated tools, as well as how employees respond to baiting attacks. If employees fail to recognise baiting attacks, then more cyber security training is required. Learn more about the internal and external penetration testing we offer at Obsidian Networks.