6 Essential IT Security Checks
5 May 2023
IT Security Basics Checklist
Threat actors, hackers and malicious people absolutely love to target, and exploit low hanging fruit that makes it easy for them to attack your IT. You can make their job a lot more difficult if you follow these Cybersecurity basics.
Are you confident that your business follows the IT Security Basics? Do you even know if you are following then? Or are you totally reliant on “hackers not wanting to target your business because what do you have that they want”?
It is time to get started to ensure that your business systems and data are safe, your employees have an understanding and awareness of IT Security and that in the event of a breach, you have a plan in place and know what to do and how to limit the damage to your business.
An average 60% of businesses that follow these guidelines are less likely to suffer a Cyber Attack. For the protection of your business, it is imperative that you are following these and ensuring that you are maintaining an active security stand point for your IT systems and employee training.
Below are some of the various items that Obsidian Networks would undertake with you and your business to ensure that you giving yourself the best possible chance to stay protected at all times.
-
Draft an Incident Response Plan
What happens if your business is part of a Cyber Attack, what would you do? Do you have an offline copy of this plan, as your entire network may be down during a Cyber Attack.
-
Draft an Information Security Policy
An Information Security Policy is a set of rules, policies and procedures designed to ensure all end users and networks within an organisation meet minimum IT security and data protection security requirements.
-
Enable Multi-Factor Authentication (MFA) on all devices
This should be enabled as standard on email, remote access and third party web applications.
-
Adopt a password management solution
Use unique, complex passwords for all systems and ensure that they have not previously been compromised in a data breach.
-
Accomplish your defence with the right security tools
This should include, Next-Generation Firewalls, Next-Generation Antivirus and Managed Endpoint Detection and Response.
-
Implement a multi-layered backup solution
This should include local and offsite backup, with scheduled disaster recovery testing.
There are more steps to these Cybersecurity Basics, this is just a base overview of what you need to be thinking about for your business IT systems.
Within the last 30 days, our firewalls have blocked nearly 200,000 malware attacks just within the UK alone.
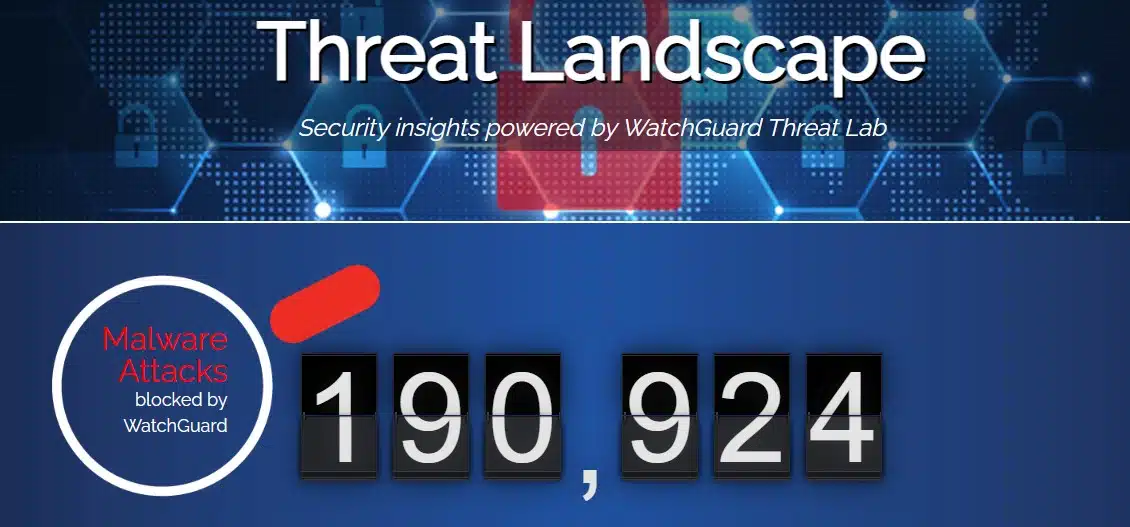
Find more information about the latest Threat Landscape
https://www.secplicity.org/threat-landscape/?s=2023-04-05&e=2023-05-04&type=all®ion=GB
If you are not sure if you are protected in the points above, it is time to get started to ensure that your business is protected and reduce your risk of a Cyber Attack.