What Actually Happens During a Cyber Attack?
26 June 2025
How you can protect your business from the inside out.
Cyber attacks are often imagined as fast, chaotic events but in reality, they’re far more silent, calculated, and damaging than most people realise.
At Obsidian Networks, we’ve seen first hand how modern attacks play out, especially for small to medium businesses. Below is a breakdown of what happens during a typical cyber attack, and what you can do to prevent it.
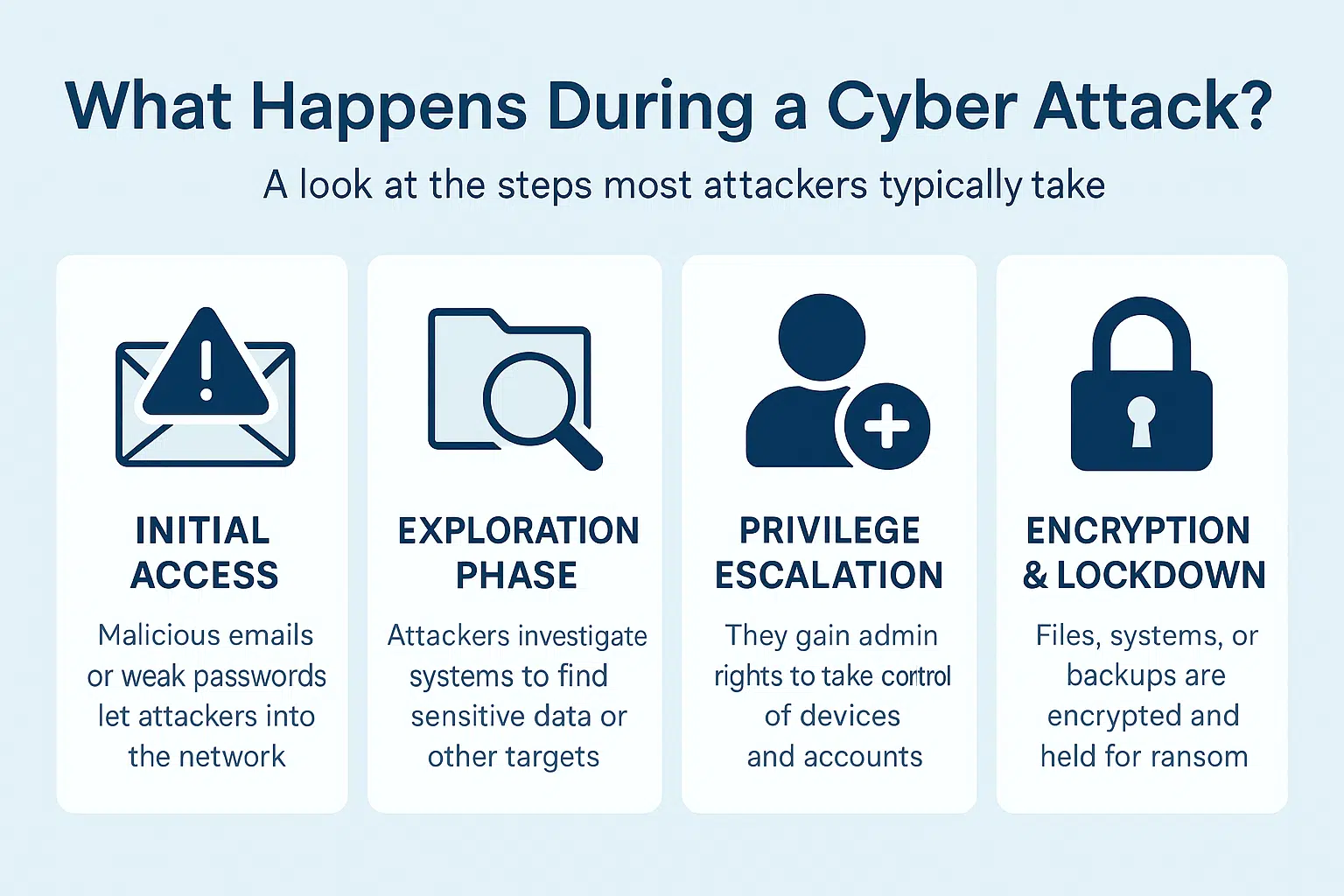
Step 1: Initial Access
Most breaches begin with something simple, potentially a staff member clicking a phishing link or using a weak password that’s already been exposed in a data breach.
Once the attacker gets a foot in the door, they don’t always launch an attack right away. They’ll wait for the right moment.
Step 2: Exploration Phase
Attackers will move around unnoticed. They look for sensitive data, shared drives, admin accounts, backup locations, and unpatched systems. This phase can last days, sometimes weeks.
They’re not after chaos yet. They’re gathering their intel to hit you when it hurts most.
Step 3: Privilege Escalation
Next, attackers aim to give themselves admin level access. That lets them disable antivirus, unlock protected files, or take over critical systems, and all this, while staying hidden.
At this point, the business is fully compromised but usually still unaware.
Step 4: Encryption & Lockdown
Only once they have full access do they launch the ransomware. Files and systems are encrypted, and a ransom note appears. Often, backups are deleted or locked first, making recovery harder if not impossible unless you have the right protections in place.
So what can you do?
The good news is that most attacks rely on common oversights and these can be fixed:
- Use multi factor authentication (MFA)
- Keep software, operating systems & firewalls patched
- Train staff to spot phishing emails
- Back up regularly and ensure that you test restore procedures
- Don’t assume your current setup is fine “because nothing’s happened yet”
Cyber security isn’t about fear, it’s about awareness. Understanding how these attacks really work helps you prepare before something goes wrong.
If you haven’t reviewed your IT setup in a while, or just want to understand your risk, start with a basic health check. It doesn’t have to be complicated.
You’ll thank yourself later.