Up Phishers Creek
15 January 2021
How Phishing works and how to defend yourself and your business
Phishing is a branch of attacks that focuses on the end user. Instead of attacking the computer, initially the attackers attempt to get the end user to click a link, enter some personal information and then the attacker, unbeknown to you can gain access into your computer, networks and even servers.
There are a few reasons for this, most companies have various security measures in place to try and prevent criminals from attacking their IT systems and data. What the attackers do is use this subset of social engineering to try to dupe your employees into clicking into an email, opening the attachment, or entering their password into a spoofed domain website.
Common Phishing Attacks
Dredge Phishing
This is an attack that you will have all seen at some point, it is a mass email sent out to a huge contact list of email addresses. This email relies on using a sheer volume of emails (often in the hundreds of thousands) and hopes that a small number of recipients will open, read, and act upon it. These emails are often ones that will claim that your email address, Paypal, online bank account or social media account has been hacked, or is in the process of being shut down.

These types of phishing emails will often have poor grammar within them. They work by trying to get the email recipient to react to the notification and the subject headline on impulse rather than the email itself attempting to fool you in a more complex method and hiding their intentions of what they are trying to do to harm your IT systems.
Another giveaway with these types of emails is if the email is not addressed to you correctly, often with messages such as Dear Sirs, Dear Madam and/or Dear Customer. Upon further inspection of the email, you will also notice that the sender email address, whilst it says Microsoft Team, it has actually has come from a random email address and a random domain. This is further indication that this email is not genuine and should be discarded and deleted at the earliest opportunity.
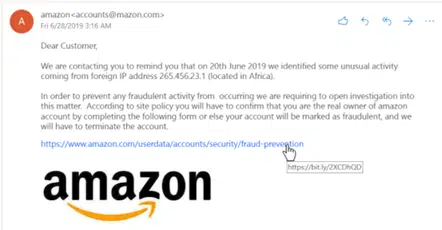
The clues in the above images that this email is not at all genuine, is upon investigating into the sender email address, you will notice that the domain name has come from mazon.com rather than the official Amazon domain name, and secondly when hovering over the link that has been provided within the email (but never clicking on it), you will see that the link actually does not go to the website that it says within the text but actually is going off to a 3rd party fake URL. In this specific instance the URL is trying to mask where it is going to completely.
Another common phishing attack is to try and blackmail the recipients by using a known combination of a username and password that they may have used in the past that has been compromised via a website or data breach. These emails will often pose as an email from an attacker claiming that they have photos and/or videos or you in dubious circumstances and asking for you to pay them a sum of money to remove and delete the evidence before they post it online and to your friends and family. These emails are a scam and as with the above, should be discarded and deleted without acknowledging the content.
Spear Phishing
Spear phishing is an attempt to attack your systems and is more malicious than dredge phishing. With this type of email, the attacker is attempting to attack a specific company or domain in a more targeted way by tailoring emails to appear more legitimate and genuine. An attacker may try and follow some of the company employees on social media and try to find specific and detailed information about the company, and their IT Support company or IT Department. They will then construct emails and send them to targeted employee email addresses so that these emails are received by the recipient and they appear and feel more plausible.
Many of the signs to identify these emails will stay the same, but the email is often hand crafted by the attackers. The chances of poor grammar, spelling mistakes and not referring to people by name is drastically reduced. Of then the domain name that the senders email has may appear to be that of a trusted source.
When investigating these types of emails, it is important to often take a second look, do not always assume that because it looks ok, then it will be. Hover your cursor over the links contained within the email, and senders address and make sure that they are going to the websites that they claim to be, and the URL has been masked or shortened. Often these types of phishing attacks are used to attempt to gain payments, often via bank transfers.
Here at Obsidian Networks, our general rule of thumb is if you see emails that are requesting bank transfers, always check with the person within your company who the email is claiming to come from and ensure that they have sent you this email, and that they want you to make the payment. Often when second guessing the email, you highlight the attack, and this is enough to know that the email is a scam and that you can discard and delete the email without any further action. Remember, a call to a colleague to confirm a large payment is never as painful as the realisation that you have sent a bank transfer to a criminal.
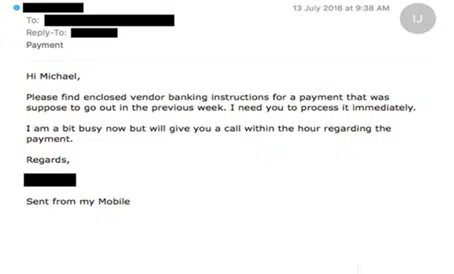
An example of a Spear Phishing email.
Whaling
This form of phishing is an offshoot of spear phishing however this is even more targeted. This usually targets the CEO, SFO or any other high profile employee/business director within the company.
When this attack takes place, the attacker attempts to swindle the recipient into either divulging critical data that can be leveraged through blackmail, theft, ransom or even access to their computer systems for further reconnaissance to extract more information from them to use against the person and/company for profit.
In 2008 there was a FBI subpoena scam where 20,000 CEO’s of businesses had been targeted by this type of attack. 2000 of these recipients have been known to fall victim. The email that was received had a browser extension integrated that told the recipient that they would need to install to view the subpoena. When they installed the extension, it was in fact a keylogger that recorded all their entries including usernames and passwords and sent all these back to servers that had been provisioned by the attackers.
Smishing
Smishing is a form of phishing that takes place via SMS or encrypted messaging systems such as WhatsApp. This style of attack are attackers posing as banks and building societies asking for personal details relating to your banking accounts. Remember, your bank will never ask you for personal details via text messages or over the telephone.
Protecting Ourselves
So, knowing the different types and levels of phishing attacks that could potentially come our way, what can you do to protect yourself and your business from these types of attacks.
- Check and verify email domain names, email addresses and any links that are contained within email messages. NEVER click on any of the links, but if the email is asking for money, or personal information and looks like it has come from a trusted source, call them, and verify that this is the case. Replying to the email may result in you replying to the attackers.
- Ensure you are using the best security for your username and passwords to website and systems. This should involve the use of 2 Factor Authentication (2FA). Should an attacker gain hold of your username and password they would also need to verify the 2FA codes. If you do receive a 2FA request and this is not you trying to do it, you will know you are under attack to deny the request and speak with your IT Support Company.
- Ensure you are running the latest Operating System security updates and patches, together with an active Anti-Virus and Anti-Malware subscription and ensure that the definitions for all are up to date and the latest release.
- Always have a good password procedure when selecting which password to use. Ensure all your passwords are unique so should one be compromised it is much easier and quicker to resolve this than having to go through every system that you use to change your passwords.
- Ensure that you have an up to date and active email filtering service that can do its best to stop and block the majority of the emails from ever reaching your inbox.
- When you do receive an email that you are unsure about, or would like a second opinion, speak with your IT Support company or IT Department. They will be able to verify the validity of the email and give you the confidence of what you should do with it next.
- If you would like more training on email phishing and what you should be looking for, speak with your IT Support company or IT Department so that they can give you the additional training that may prevent you from falling victim in the future.
If you feel that you or your business could benefit from Cyber Security Training, email filtering, 2FA systems or Anti-Virus solutions our team at Obsidian Networks can help bring peace of mind to you and your business to ensure that your IT systems are secure and protected.